chisel 也可以用于反向的内网穿透,此时它的功能与 Mr.2 类似,当然还有一些类似的软件,如:nps,frp 等都可以实现类似的功能。
注意:以下示例省略了认证信息的设置,具体的设置请参考 chisel --key, --auth, --fingerprint 等选项。
方案一
如图所示:
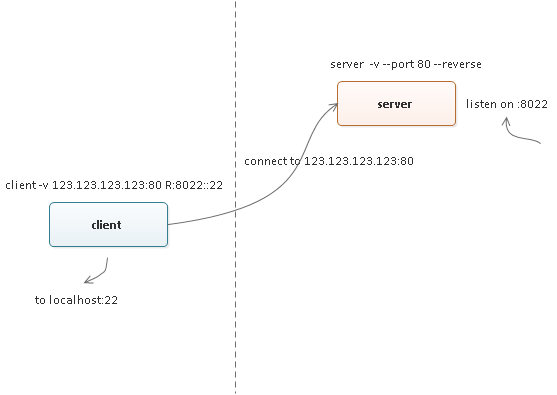
服务端
外网机器(IP 地址为 123.123.123.123)启动 chisel 服务端,在 80 端口上接收 chisel 客户端的连接:
$ chisel server -v --port 80 --reverse
2019/09/20 07:54:06 server: Reverse tunnelling enabled
2019/09/20 07:54:06 server: Fingerprint 34:91:c0:5d:ec:50:ef:10:53:dc:00:aa:2f:d2:49:51
2019/09/20 07:54:06 server: Listening on 0.0.0.0:80...
2019/09/20 07:54:06 server: session#1: Handshaking...
2019/09/20 07:54:06 server: session#1: Verifying configuration
2019/09/20 07:54:06 server: session#1: Open
2019/09/20 07:54:06 server: proxy#1:R:0.0.0.0:8022=>0.0.0.0:22: Listening
选项 -v 表示 verbose。
客户端
内网机器启动 chisel 客户端,连接至外网的 chisel 服务端 123.123.123.123:80
$ chisel client -v 123.123.123.123:80 R:8022::22
2019/09/20 07:59:57 client: Connecting to ws://123.123.123.123:80
2019/09/20 07:59:57 client: Handshaking...
2019/09/20 07:59:57 client: Fingerprint 34:91:c0:5d:ec:50:ef:10:53:dc:00:aa:2f:d2:49:51
2019/09/20 07:59:57 client: Sending config
2019/09/20 07:59:57 client: Connected (Latency 1.197951ms)
注意参数 R:8022::22 表示外网 chisel 服务端将打开监听端口 8022,并将访问 8022 端口的 TCP 流量转发至内网的 22 端口,实际效果就是此时如果访问外网 123.123.123.123:8022 就会访问内网的 localhost:22:
$ lsb_release -i
Distributor ID: CentOS
$ ssh 123.123.123.123 -p 8022
The authenticity of host '[123.123.123.123]:8022 ([123.123.123.123]:8022)' can't be established.
ECDSA key fingerprint is 42:21:98:26:36:53:98:90:ca:d8:ea:80:54:0d:64:c9.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '[123.123.123.123]:8022' (ECDSA) to the list of known hosts.
runsisi@123.123.123.123's password:
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-58-generic x86_64)
...
注意:chisel 在 remote 参数的解析上很灵活,比如 R:8022::22 实际上是 R:8022:localhost:22,也可以写成 R:8022:22,说实话,我觉得这种处理很混乱。
方案二
显然,方案一所示的内网穿透方案仍然是一种简单的端口映射方式,如果要允许 socks5 代理形式的穿透,则需要在方案一的基础上再搭建一组 chisel 服务(chisel 的 --socks5 参数仅支持在服务端指定,方案一建立的连接作为一个传输通道),方案如下图所示:
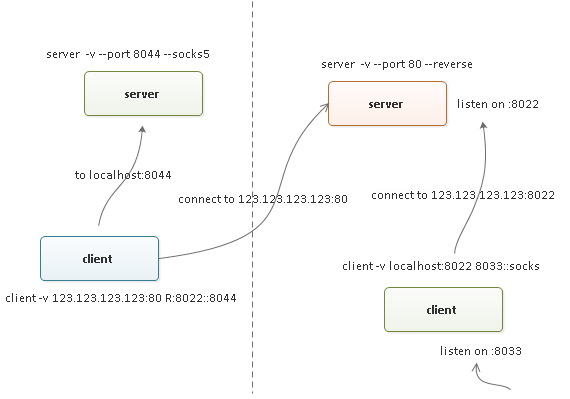
首先基于方案一建立反向的通道(端口示例稍有调整):
chisel 服务端
$ chisel server -v --port 80 --reverse
2019/09/20 12:25:42 server: Reverse tunnelling enabled
2019/09/20 12:25:42 server: Fingerprint 5b:95:a6:f8:f0:f0:3c:e1:ac:9a:b7:18:69:a6:90:f1
2019/09/20 12:25:42 server: Listening on 0.0.0.0:80...
chisel 客户端
$ chisel client -v 123.123.123.123:80 R:8022::8044
2019/09/20 12:32:27 client: Connecting to ws://123.123.123.123:80
2019/09/20 12:32:27 client: Handshaking...
2019/09/20 12:32:27 client: Fingerprint 5b:95:a6:f8:f0:f0:3c:e1:ac:9a:b7:18:69:a6:90:f1
2019/09/20 12:32:27 client: Sending config
2019/09/20 12:32:27 client: Connected (Latency 2.314245ms)
socks5 代理服务端
$ chisel server -v --port 8044 --socks5
2019/09/20 12:33:29 server: SOCKS5 server enabled
2019/09/20 12:33:29 server: Fingerprint 2e:4a:18:33:65:34:78:09:41:b6:78:75:6b:4b:bd:c3
2019/09/20 12:33:29 server: Listening on 0.0.0.0:8044...
socks5 代理接入端
$ ./chisel client -v localhost:8022 8033::socks
2019/09/20 12:31:04 client: Connecting to ws://localhost:8022
2019/09/20 12:31:04 client: proxy#1:127.0.0.1:8033=>socks: Listening
2019/09/20 12:31:04 client: Handshaking...
2019/09/20 12:31:04 client: Fingerprint 2e:4a:18:33:65:34:78:09:41:b6:78:75:6b:4b:bd:c3
2019/09/20 12:31:04 client: Sending config
2019/09/20 12:31:04 client: Connected (Latency 2.627081ms)
使用 :8033 作为 socks5 代理服务地址,即可访问内网(CentOS 下示例):
$ nc localhost 22
SSH-2.0-OpenSSH_6.6.1
$ nc -4 --proxy-type socks5 --proxy localhost:8033 localhost 22
SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.3
方案三
方案二中,我们费这么大劲,折腾的这么复杂实际上仅仅只是为了在内网启动一个 socks5 的代理服务端,实际上我们完全可以用另外的工具进行替换,如 gost,方案如下图所示:
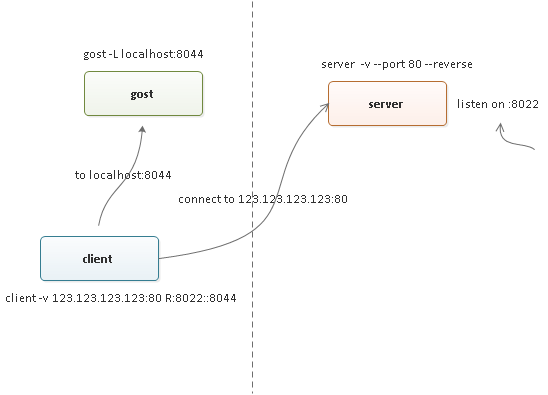
首先基于方案一建立反向的通道(端口示例稍有调整):
chisel 服务端
$ chisel server -v --port 80 --reverse
2019/09/20 13:48:25 server: Reverse tunnelling enabled
2019/09/20 13:48:25 server: Fingerprint 32:55:7c:cb:77:a7:3a:9c:1e:b6:03:eb:ec:9a:17:29
2019/09/20 13:48:25 server: Listening on 0.0.0.0:80...
chisel 客户端
$ chisel client -v 123.123.123.123:80 R:8022::8044
2019/09/20 13:52:53 client: Connecting to ws://123.123.123.123:80
2019/09/20 13:52:53 client: Handshaking...
2019/09/20 13:52:53 client: Fingerprint 32:55:7c:cb:77:a7:3a:9c:1e:b6:03:eb:ec:9a:17:29
2019/09/20 13:52:53 client: Sending config
2019/09/20 13:52:53 client: Connected (Latency 1.237862ms)
gost 代理
$ gost -L localhost:8044
2019/09/20 13:53:04 route.go:479: auto://localhost:8044 on 127.0.0.1:8044
使用 :8022 作为 socks5 代理服务地址,即可访问内网(CentOS 下示例):
$ nc localhost 22
SSH-2.0-OpenSSH_6.6.1
$ nc -4 --proxy-type socks5 --proxy localhost:8022 localhost 22
SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.3
最后修改于 2019-09-20