OpenLDAP 本质上是一个数据库,而它的使用也与 SQL 数据库类似,包括两部分,一是 OpenLDAP 自身的配置,一是用户数据的增删改查。
上一篇文章提到,新版本的 OpenLDAP 将其自身的配置从传统的配置文件统一为独立的 DIT 进行管理,管理员可以使用以往所熟悉的管理用户数据的那一套工具管理其自身的配置。
ldapuri
LDAP 支持三种形式的 URI:ldap://[host][:port>], ldaps://[host][:port], ldapi://[path]
host 默认为 localhost,ldap 端口默认为 389,ldaps 端口默认为 636.
访问/修改配置数据需要通过 root 用户使用 ldapi://(即本地 unix socket)进行连接。
unix socket 的默认路径为 /var/run/ldapi:
$ ll /var/run/ldapi
lrwxrwxrwx 1 root root 11 Jun 5 16:57 /var/run/ldapi -> slapd/ldapi=
如果需要显示指定路径,需要将 / 进行 URL 编码,即转换为 %2F 或 %2f(大小写无关):
$ unicode /
U+002F SOLIDUS
UTF-8: 2f UTF-16BE: 002f Decimal: / Octal: \057
/
category: [Po (Punctuation, Other)]
Unicode block: 0000..007F; Basic Latin
Bidi: CS (Common Number Separator)
$ ldapsearch -H ldapi://%2Fvar%2Frun%2Fldapi -x -b '' -s base '+'
# extended LDIF
#
# LDAPv3
# base <> with scope baseObject
# filter: (objectclass=*)
# requesting: +
#
#
dn:
structuralObjectClass: OpenLDAProotDSE
configContext: cn=config
namingContexts: dc=runsisi,dc=com
supportedControl: 2.16.840.1.113730.3.4.18
...
访问 root DSE
$ ldapsearch -H ldapi:// -x -s base -b '' '+'
# extended LDIF
#
# LDAPv3
# base <> with scope baseObject
# filter: (objectclass=*)
# requesting: +
#
#
dn:
structuralObjectClass: OpenLDAProotDSE
configContext: cn=config
namingContexts: dc=runsisi,dc=com
supportedControl: 2.16.840.1.113730.3.4.18
...
$ ldapsearch -H ldap:// -x -s base -b '' '+'
# extended LDIF
#
# LDAPv3
# base <> with scope baseObject
# filter: (objectclass=*)
# requesting: +
#
#
dn:
structuralObjectClass: OpenLDAProotDSE
configContext: cn=config
namingContexts: dc=runsisi,dc=com
supportedControl: 2.16.840.1.113730.3.4.18
...
配置数据管理
使用 ldapmodify
增加字段:
$ vi add.ldif
dn: olcDatabase={2}mdb,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}UNC/GjBr74HdBGx92smagS0sjP0HhT2u
$ sudo ldapmodify -H ldapi:// -Y EXTERNAL -f add.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={2}mdb,cn=config"
删除字段:
$ vi delete.ldif
dn: olcDatabase={2}mdb,cn=config
changetype: modify
delete: olcRootPW
$ sudo ldapmodify -H ldapi:// -Y EXTERNAL -f delete.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={2}mdb,cn=config"
更新字段:
$ vi replace.ldif
dn: olcDatabase={2}mdb,cn=config
changetype: modify
replace: olcRootPW
olcRootPW: {SSHA}UNC/GjBr74HdBGx92smagS0sjP0HhT2u
$ sudo ldapmodify -H ldapi:// -Y EXTERNAL -f replace.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={2}mdb,cn=config"
可以同时修改多个字段:
$ vi xxx.ldif
dn: olcDatabase={2}mdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=runsisi,dc=com
-
replace: olcRootDN
olcRootDN: cn=admin,dc=runsisi,dc=com
-
delete: olcRootPW
-
add: olcRootPW
olcRootPW: {SSHA}tWFrurFrTXu9ypiNpEB0BTTF89LdhJaW
-
replace: olcRootPW
olcRootPW: {SSHA}tWFrurFrTXu9ypiNpEB0BTTF89LdhJaW
$ sudo ldapmodify -H ldapi:// -Y EXTERNAL -f xxx.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={2}mdb,cn=config"
也可以每个字段完全独立进行修改:
$ vi xxx2.ldif
dn: olcDatabase={2}mdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=runsisi,dc=com
dn: olcDatabase={2}mdb,cn=config
changetype: modify
replace: olcRootDN
olcRootDN: cn=admin,dc=runsisi,dc=com
dn: olcDatabase={2}mdb,cn=config
changetype: modify
delete: olcRootPW
dn: olcDatabase={2}mdb,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}tWFrurFrTXu9ypiNpEB0BTTF89LdhJaW
dn: olcDatabase={2}mdb,cn=config
changetype: modify
replace: olcRootPW
olcRootPW: {SSHA}tWFrurFrTXu9ypiNpEB0BTTF89LdhJaW
$ sudo ldapmodify -H ldapi:// -Y EXTERNAL -f xxx2.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={2}mdb,cn=config"
modifying entry "olcDatabase={2}mdb,cn=config"
modifying entry "olcDatabase={2}mdb,cn=config"
modifying entry "olcDatabase={2}mdb,cn=config"
modifying entry "olcDatabase={2}mdb,cn=config"
配置 acl:
$ vi access.ldif
dn: olcDatabase={2}mdb,cn=config
changetype: modify
add: olcAccess
olcAccess: {0}to * by dn="cn=user1,dc=runsisi,dc=com" write by * read
$ sudo ldapmodify -H ldapi:// -Y EXTERNAL -f access.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={2}mdb,cn=config"
使用 ldapvi
首先需要安装 ldapvi 工具。
接下来的操作和 vi 一致:
$ sudo ldapvi -h ldapi:// -Y EXTERNAL -b cn=config
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
7 entries read
# -*- coding: utf-8 -*-
# http://www.lichteblau.com/ldapvi/manual#syntax
# SASL output:
# SASL/EXTERNAL authentication started
# SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
# SASL SSF: 0
0 cn=config
objectClass: olcGlobal
cn: config
olcArgsFile: /var/run/openldap/slapd.args
olcPidFile: /var/run/openldap/slapd.pid
...
用户数据管理
命令行工具
添加:
$ vi user.ldif
dn: cn=user1,dc=runsisi,dc=com
objectClass: simpleSecurityObject
objectClass: organizationalRole
cn: user1
description: OpenLDAP user
userPassword: {SSHA}UNC/GjBr74HdBGx92smagS0sjP0HhT2u
$ ldapadd -H ldap:// -x -W -D cn=admin,dc=runsisi,dc=com -f user.ldif
Enter LDAP Password:
adding new entry "cn=user1,dc=runsisi,dc=com"
注意:ldapadd 是 ldapmodify 的硬链接(hard link),因此也可以使用如下的命令:
$ ldapmodify -a -H ldap:// -x -W -D cn=admin,dc=runsisi,dc=com -f user.ldif
Enter LDAP Password:
adding new entry "cn=user1,dc=runsisi,dc=com"
ldap_add: Already exists (68)
删除:
$ ldapdelete -H ldap:// -x -D cn=admin,dc=runsisi,dc=com cn=user1,dc=runsisi,dc=com -W
Enter LDAP Password:
查找:
$ ldapsearch -H ldap:// -x -D cn=admin,dc=runsisi,dc=com -b dc=runsisi,dc=com -W
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base <dc=runsisi,dc=com> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# runsisi.com
dn: dc=runsisi,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
dc: runsisi
o: my own company
...
使用 ldapvi 进行编辑会更简单:
$ ldapvi -h ldap://10.120.123.234 -D cn=admin,dc=runsisi,dc=com -b dc=runsisi,dc=com
--- Login
Type M-h for help on key bindings.
Filter or DN: cn=admin,dc=runsisi,dc=com
Password: ******
1 entry read
usage: which [-as] program ...
usage: which [-as] program ...
usage: which [-as] program ...
# -*- coding: utf-8 -*- vim:fileencoding=utf-8:
# http://www.lichteblau.com/ldapvi/manual#syntax
0 dc=runsisi,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
dc: runsisi
o: my own company
...
图形界面工具
phpLDAPadmin
$ docker pull osixia/phpldapadmin
$ docker run -idt --rm --net host -e PHPLDAPADMIN_LDAP_HOSTS=localhost osixia/phpldapadmin
然后访问 https://localhost/ 即可:
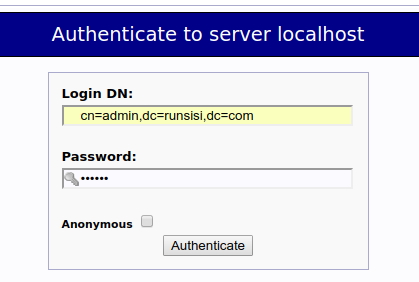
Apache Directory Studio
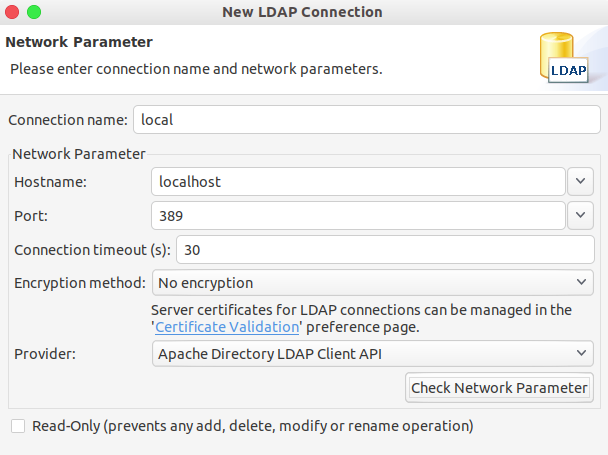
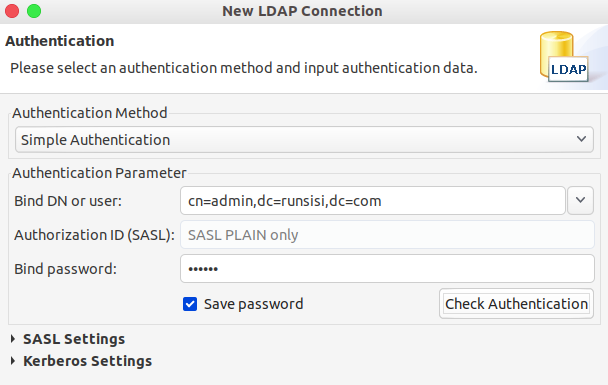
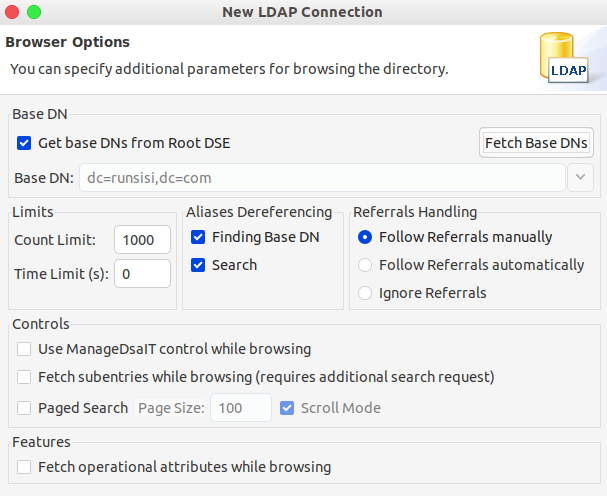
参考资料
LDAP 基础学习笔记(概念 & 快速安装)
https://zhuanlan.zhihu.com/p/32732045
Basic LDAP Concepts
https://ldap.com/basic-ldap-concepts/
Basics OpenLDAP Tutorial for Beginners – Understanding Terminologies & Usage
https://www.golinuxcloud.com/ldap-tutorial-for-beginners-configure-linux/
Understanding the LDAP Protocol, Data Hierarchy, and Entry Components
How To Configure OpenLDAP and Perform Administrative LDAP Tasks
A docker image to run phpLDAPadmin
https://github.com/osixia/docker-phpLDAPadmin
URL Encoding
http://www.blooberry.com/indexdot/html/topics/urlencoding.htm
最后修改于 2019-06-06